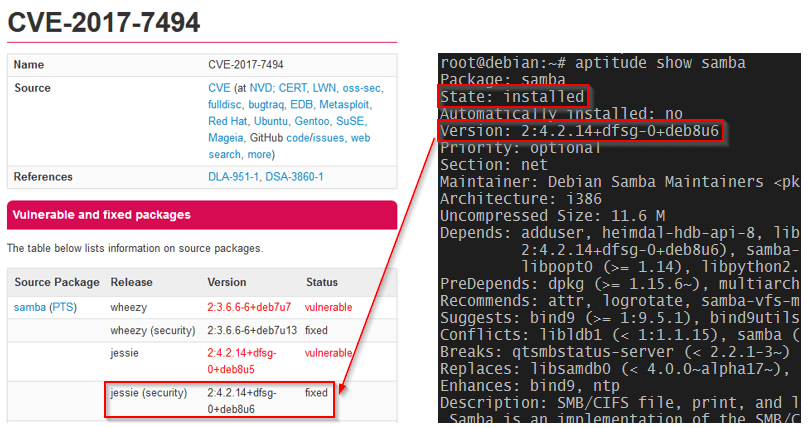
Security advisories are published by leading Linux O.S. distributors, announcing important security patches that should be applied as a matter of urgency to safeguard a particular piece of software and ultimately, safeguard your Linux Operating System.
Different Linux flavours can be set up to automatically email a notification to you. You can also set up automated security patching. I will show you how below.
Below are several links to visit for Security advisory notices and details.
http://www.linuxsecurity.com/content/section/3/170/ - Shows Security advisories for several flavours of Linux O.S.
https://www.debian.org/security/ - Shows Security advisories for Debian
https://www.ubuntu.com/usn/ - Shows Security advisories for Ubuntu
Prerequisites
Before we get started:
- You have to have an SMTP server that can send the emails from your workstation, to the recipient (i.e. your corporate exchange or Gmail).
- You have the credentials for a user that is able to send Email on that server (i.e. a mailbox or a Gmail account).
There are a few simple SMTP servers out there. The ssmtp (Simple S.M.T.P) package works well. There are better setup articles but we can quickly set it up.
To install the ssmtp (Simple S.M.T.P) package, use the following command:
sudo apt-get install ssmtp
Using your favourite editor, edit the configuration file:
sudo nano /etc/ssmtp/ssmtp.conf
Edit the following lines. The number after the colon, is the port number used to connect to your email providers SMTP service.
root=username@gmail.com
mailhub=smtp.gmail.com:587
hostname=username@gmail.com
UseSTARTTLS=YES
AuthUser=username
AuthPass=password
FromLineOverride=yes
In order to make the default (root) “from” field be the server name, edit the /etc/ssmtp/revaliases file:
root:machine-name@some-domain.com:smtp.gmail.com
Test the ssmtp setup by sending an Email:
echo "Test message using ssmtp" | sudo ssmtp -vvv your-email@some-domain.com
Security Update email alerts for Debian/Ubuntu
Apticron is a simple script which sends daily emails about pending package updates such as security updates.
sudo apt-get install apticron
Configure Apticron
sudo nano /etc/apticron/apticron.conf
Edit the following line, ‘EMAIL=’ changing it to your email address
# apticron.conf
#
# set EMAIL to a space separated list of addresses which will be notified of
# impending updates
#
EMAIL="root"
[...]
You will now receive an email alert once a day if, there are any security advisories.
Automatic Security Updates
To check if your Debian / Ubuntu system has Automatic Security Updates installed, you can manually run it with verbose.
sudo apt-get update
sudo unattended-upgrades -v
If this gives an error then, it is not installed so execute
sudo dpkg-reconfigure --priority=low unattended-upgrades
Once installed, check
cat /etc/apt/apt.conf.d/20auto-upgrades
This should result in
APT::Periodic::Update-Package-Lists "1";
APT::Periodic::Unattended-Upgrade "1";
If not, edit the file and set APT::Periodic::Unattended-Upgrade to "1".
References:
https://help.ubuntu.com/community/AutomaticSecurityUpdates
https://www.quora.com/How-can-I-get-email-alerts-for-Linux-security-patches-mainly-Ubuntu-CentOS
http://www.linuxsecurity.com/content/section/3/170/
https://www.debian.org/security/
https://www.ubuntu.com/usn/