In May 2017 systems worldwide were hit by the WannaCry ransomware. If you get infected then, then your personal files will be encrypted and a pop up message appears to say that you must pay a ransom (usually BitCoins) or, risk losing your precious files. If you have backed up your files recently then, congratulations. Wipe and reinstall your infected PC / system and recover your backups. If you didn't back up recently, too bad. You don't expect the criminals to really give you your files back after paying the (first) ransom do you!?
Stay ahead of the criminals and ensure your PC / systems are security patched automatically, before you get hit by the latest flavour of virus / ransomware.
Below are link and tips on how to protect yourself against WannaCry 2017.
Debian / Ubuntu
Well, if you have set up automatic security updates on your Debian or, Ubuntu as I mentioned in my Dirty COW exploit and Automatic Security Updates article then, you're already fixed for this exploit.
Whether you just want to check that you've patched or, want to patch your systems yourself, head over to the Tecmint article, How to Fix SambaCry Vulnerability (CVE-2017-7494) in Linux Systems.
In a nutshell
Check if you are already patched.
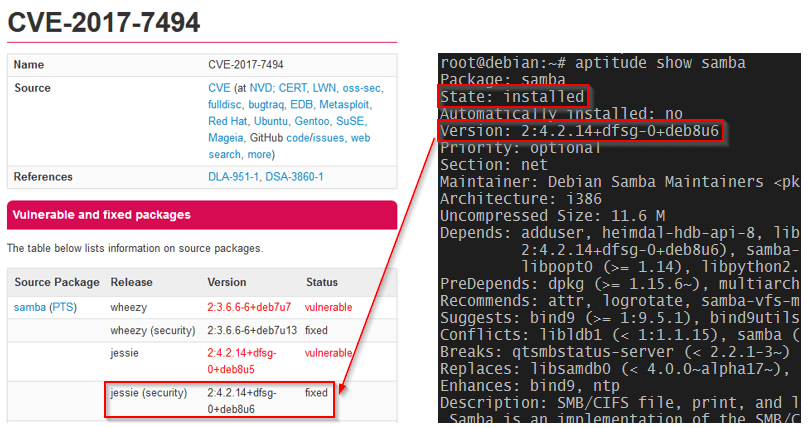
Image from tecmint.com
Visit my blog page above and configure your Debian / Ubuntu system to automatically install security updates.
Windows
Check out BitDefender's article, WannaCry wreaks havoc. How to keep your business safe.In a nutshell
Visit, Microsoft Security Bulletin MS17-010 - Critical and ensure you download and patch your Window's version. Configure your Windows systems to automatically install Security Updates.
No comments:
Post a Comment